安卓逆向 - 基础入门教程
本文转自小馒头yy 并作补充
一、引言
上篇文章:安卓逆向 - 基础入门教程_小馒头yy的博客-CSDN博客 介绍了Frida的安装、基本使用,今天我们来看看Frida常用Hook和基于Frida抓包实践。
二、Frida常用 Hook脚本
1、hook java.net.URL
2
3
4
5
6
7
8
var URL = Java.use('java.net.URL');
URL.$init.overload('java.lang.String').implementation = function (a) {
console.log('加密前:' + a)
showStacks()
this.$init(a)
}
}2、hook okhttp3 HttpUrl
2
3
4
5
6
7
8
9
10
var Builder = Java.use('okhttp3.Request$Builder');
Builder.url.overload('okhttp3.HttpUrl').implementation = function (a) {
console.log('a: ' + a)
var res = this.url(a);
showStacks()
console.log("res: " + res)
return res;
}
}3、hook okhttp3 addHeader
2
3
4
5
6
7
8
9
10
11
var Builder = Java.use("okhttp3.Request$Builder");
Builder["addHeader"].implementation = function (str, str2) {
console.log("key: " + str)
console.log("val: " + str2)
showStacks()
var result = this["addHeader"](str, str2);
console.log("result: " + result);
return result;
};
}4、打印堆栈
2
3
4
5
Java.perform(function () {
console.log(Java.use("android.util.Log").getStackTraceString(Java.use("java.lang.Exception").$new()));
});
}5、hook Base64
2
3
4
5
6
7
8
9
// Base64
var Base64Class = Java.use("android.util.Base64");
Base64Class.encodeToString.overload("[B", "int").implementation = function (a, b) {
var rc = this.encodeToString(a, b);
console.log(">>> Base64 " + rc);
return rc;
}
}6、hook HashMap
2
3
4
5
6
7
8
var Build = Java.use("java.util.HashMap");
Build["put"].implementation = function (key, val) {
console.log("key : " + key)
console.log("val : " + val)
return this.put(key, val)
}
}
三、某麦网抓包实践
本篇以某麦网帖子详情接口,演示如何基于Frida hook抓包
1、安装某麦网8...apk
2、搭建Frida hook 环境,注入 hook java.net.URL脚本
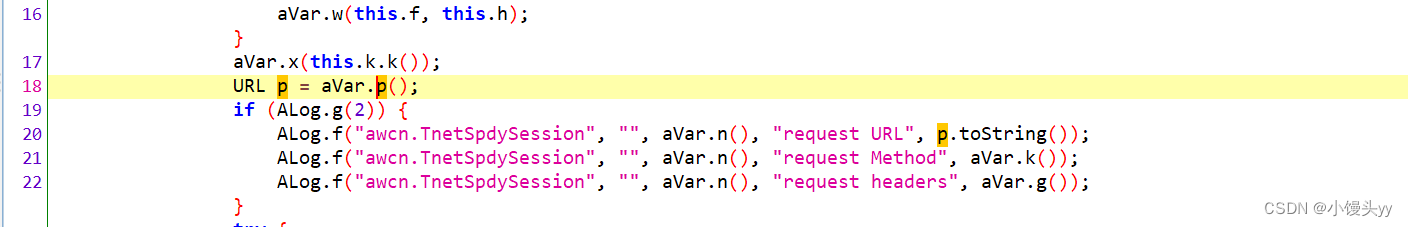
3、点进帖子详情打印出如下堆栈,我们可以根据打印出的信息,跟栈分析该接口的请求头。
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
java.lang.Exception
at java.net.URL.<init>(Native Method)
at tb.yy0.m(Taobao:1)
at anet.channel.request.a.p(Taobao:2)
at anet.channel.session.TnetSpdySession.w(Taobao:18)
at anetwork.channel.unified.NetworkTask.sendRequest(Taobao:6)
at anetwork.channel.unified.NetworkTask.run(Taobao:44)
at anetwork.channel.unified.UnifiedRequestTask$a.proceed(Taobao:15)
at com.taobao.orange.sync.NetworkInterceptor.intercept(Taobao:30)
at anetwork.channel.unified.UnifiedRequestTask$a.proceed(Taobao:7)
at anetwork.channel.unified.UnifiedRequestTask$3.run(Taobao:2)
at java.util.concurrent.Executors$RunnableAdapter.call(Executors.java:428)
at java.util.concurrent.FutureTask.run(FutureTask.java:237)
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1133)
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:607)
at java.lang.Thread.run(Thread.java:761)4、使用Jadx打开某麦网apk
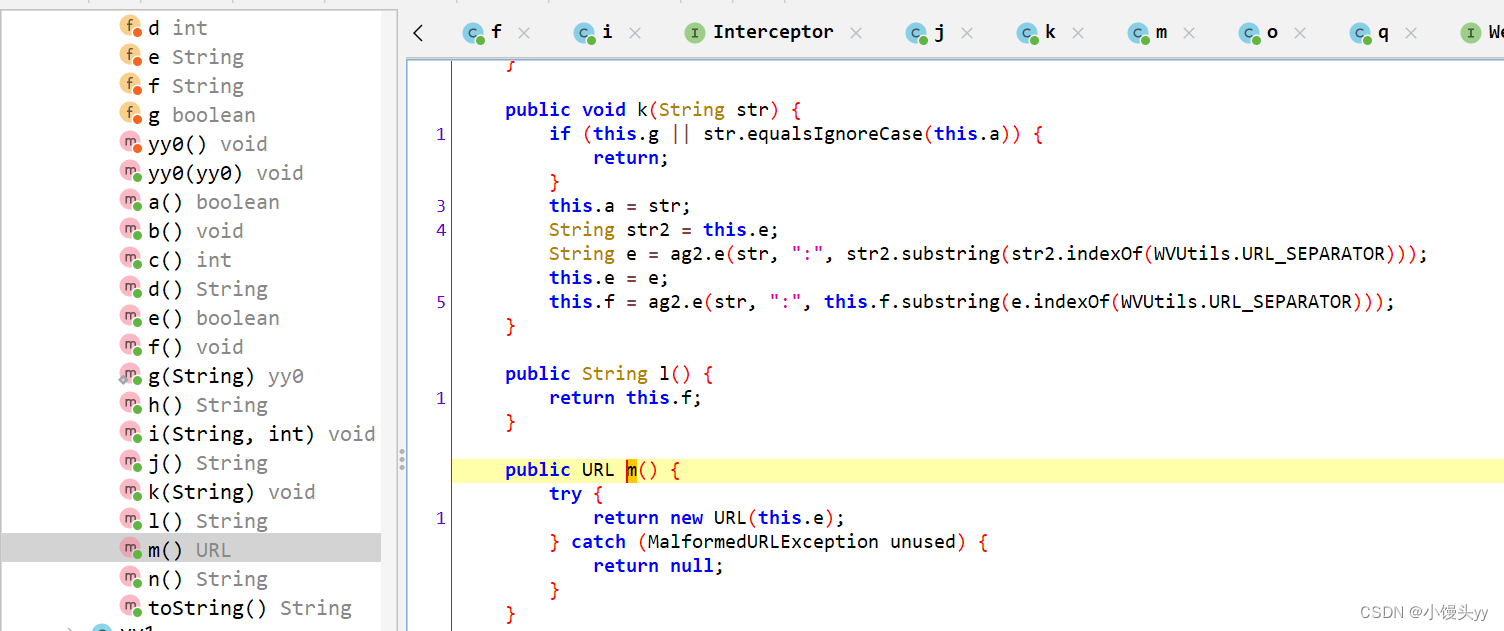
从at tb.yy0.m(Taobao:1)跟栈分析
根据调用栈往上走,定位到如下位置,注意这行代码:
代码注释很清楚了 request headers,我们跟进 hook aVar.g() 这个方法
2
3
return Collections.unmodifiableMap(this.f);
}hook之,对象输出可以使用 JSONObject转一下
2
3
4
5
6
7
8
9
var JSONObject = Java.use("com.alibaba.fastjson.JSONObject");
var a = Java.use("anet.channel.request.a");
a["g"].implementation = function () {
var result = this["g"]();
console.log("result : " + JSONObject.toJSON(result).toString());
return result;
};
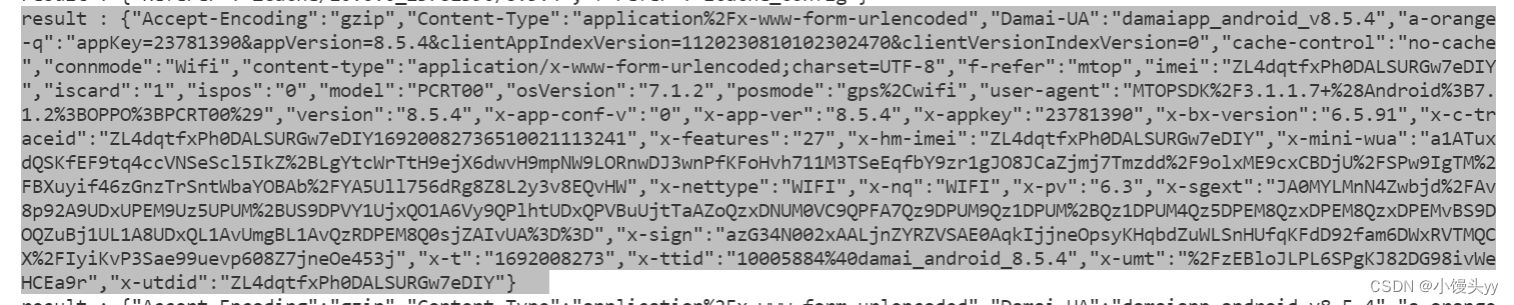
}打印出如下内容:
请求 URL、 请求方法这边都写得很清楚啦。
收工!